If you're looking for a way to circumvent Microsoft's Windows 11 system requirements, don't go clicking on any old website and downloading an installer. To be expected, nefarious actors have already loaded up a fake Windows 11 installer onto the web and are installing malware onto users' PCs while they attempt to install the latest OS.
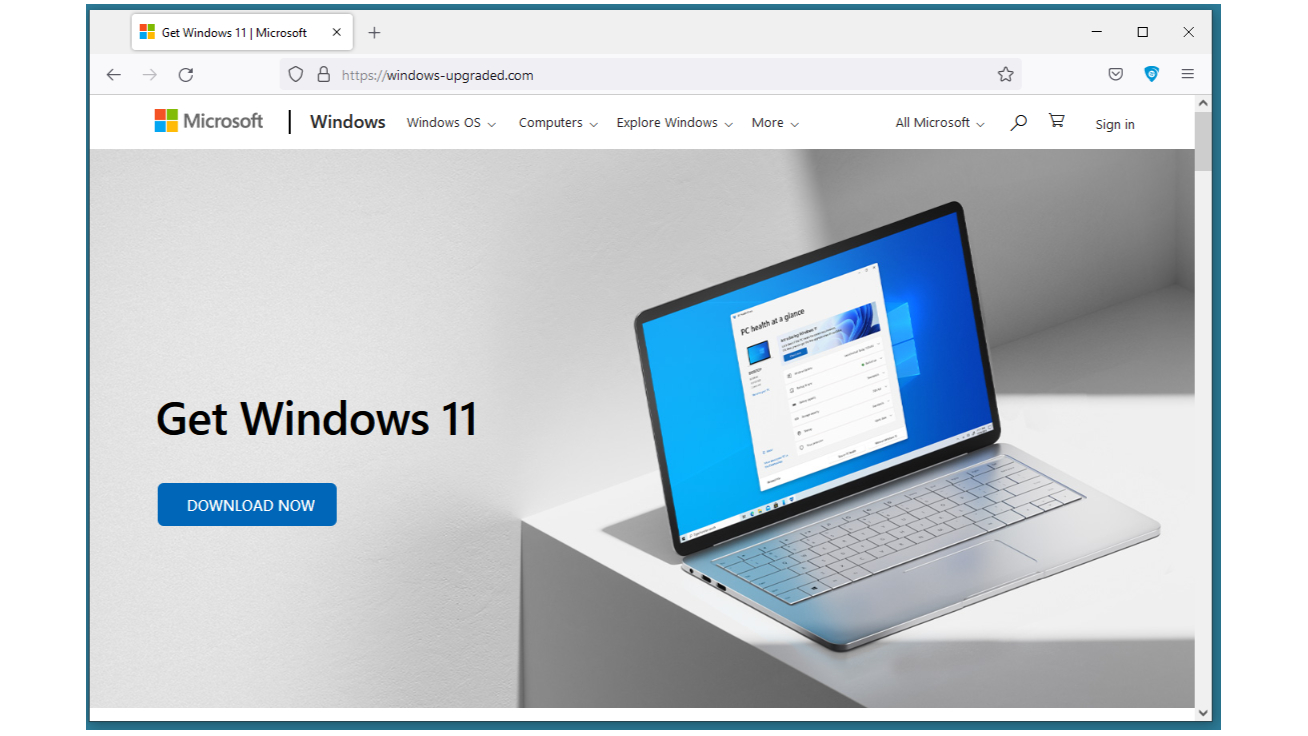
A website going by the name windows-upgraded[dot]com was recently analysed by HP's threat research team, and they found it attempting to distribute RedLine Stealer, a piece of malware that sets out to steal user information.
The website, as pictured by HP below (I don't recommend you visit it personally), looks like a mirror image of Microsoft's own Windows 11 installer website. However, beneath the “Get Windows 11” banner, the button labelled “Download Now” leads to a dodgy installer hosted on Discord's content delivery network (CDN).
The installer is called Windows11InstallationAssistant.zip, and it's only 1.5MB big compressed. It contains six Windows DLLs, an XML file, and a portable executable file. Once uncompressed, the file weighs in at 753MB, and therein lies some clue as to its nefarious intent.
“Since the compressed size of the zip file was only 1.5 MB, this means it has an impressive compression ratio of 99.8%,” HP researchers say. “This is far larger than the average zip compression ratio for executables of 47%. To achieve such a high compression ratio, the executable likely contains padding that is extremely compressible. Viewed in a hex editor, this padding is easily spotted.”
The padding looks like a bunch of 0x30 byte codes and has no impact on the operation of the file. This may also be there as a way to circumvent anti-virus scans, HP suggests, as these may not attempt to completely scan a file of this size.
When the file is run, it goes through the motions of downloading and running the RedLine Stealer malware, which attempts to steal user information, passwords, credit card information, and cryptocurrency wallets. It will then attempt to phone home to an IP address and send this information to the attackers.
As HP notes, this is also similar to another attack that it analysed in 2021. Attackers used a similar spoof technique to set up a Discord webpage with a closely related but misspelt name to trick users into downloading a dangerous installer posing as Discord's own. HP notes that this attack used the same DNS servers, malware, and domain registrar as the Windows 11 one.
As for Windows 11, there are ways to download it securely. Microsoft is releasing the new OS, launched in October, to compatible PCs gradually. That said, not every PC will be offered Windows 11, and that's down to security-based system requirements that the OS depends upon.
If you're in that boat, with an older CPU that's not compatible with Windows 11, we do not recommend searching the web for an ISO or installer. Instead, you may be able to install the OS via Microsoft's official downloads page, using a Windows 11 ISO or installation media. There are some concerns here, though. Microsoft won't guarantee that you'll receive critical updates this way, and you may be left with an insecure build of your OS.
For security, then, the best thing to do is sit tight until you upgrade your hardware down the line. Windows 11 isn't much of a departure from Windows 10, really, so you're not missing out on a whole lot but rounded corners. Even Windows 11's best upcoming gaming feature, DirectStorage, is set to arrive on Windows 10.

Discord as a target and host for malware
Security company Sophos warned last year that Discord has become a hub for malware. At that time, it recorded 4% of TLS-protected malware downloads came from Discord, as it offers a way for bad actors to upload files and share them with others. Due to this platform's popularity, it's expected that gamers may be prime targets for malware on the service.
Discord is not alone in its ability to host bad files. Any user-generated platform is open to exploitation. It just so happens that Discord, the popular VoIP service, has grown so much in popularity and scope that it's been both the target of attackers looking to exploit its millions of users and those looking to exploit its CDN for file hosting of malware.
Recently security researchers at Microsoft-owned RiskIQ outlined how Discord's CDN can, and has, been used to host various types of malware.
It reports that a common way for attackers to get said malware onto users' computers is by linking out to a Discord domain with a link in the format: hxxps://cdn.discordapp[.]com/attachments/{ChannelID}/{AttachmentID}/{filename}. This URL could then be linked to by an attacker to redirect a user from another, more legitimate-looking URL to a Discord server hosting dodgy files.

Best gaming motherboard: the best boards around
Best AMD motherboard: your new Ryzen's new home
The most common type of malware discovered by RiskIQ was a trojan, intended to spoof the appearance of a real app or download. The aforementioned Windows 11 installer download, for example. However, it also found evidence of 27 unique malware types hosted on Discord's CDN.
It's not just direct malware that's a threat, either, scammers recently took hold of an NFT services' vanity URL on Discord and redirected it to their own scam Discord server. The issue here being CryptoBatz simply changed their discord URL without adjusting all previous messaging on social media to reflect the change, and the scammers then took the old URL as their own. The scammers may have made as much as $40,000 from this mess alone.
Security researchers are doing their part to report these issues to Discord, and Discord is trying to stamp out malware as best it can, but where one door closes another opens. Since that's been true since the dawn of computers, we recommend sticking to age-old advice and staying cautious about unofficial websites and downloads. Some caution regarding links in Discord servers now appears advisable, too.